How to Create Stunning Anime Videos Using AI Anime Tools

Anime has been a captivating art form for decades, with its rich visuals, compelling characters, and emotional storytelling. But, creating ...
Read moreThehrwp And The Future Of People Management

People management is evolving faster than ever before. Organizations are moving away from traditional, rigid management structures and embracing modern, ...
Read moreWhy Invest In Tanning Salon Software Solutions?

A packed appointment book sounds great, until it turns into chaos. One no-show, a last-minute reschedule, or a double-booked bed, ...
Read moreSwap Face AI Free: How to Transform Your Photos Instantly

Artificial Intelligence has revolutionized photo editing, making it easier than ever to create fun and creative images. One of the ...
Read moreContent Creation Made Effortless — How Influencers and Creatives Use VisualGPT’s AI Clothes Changer
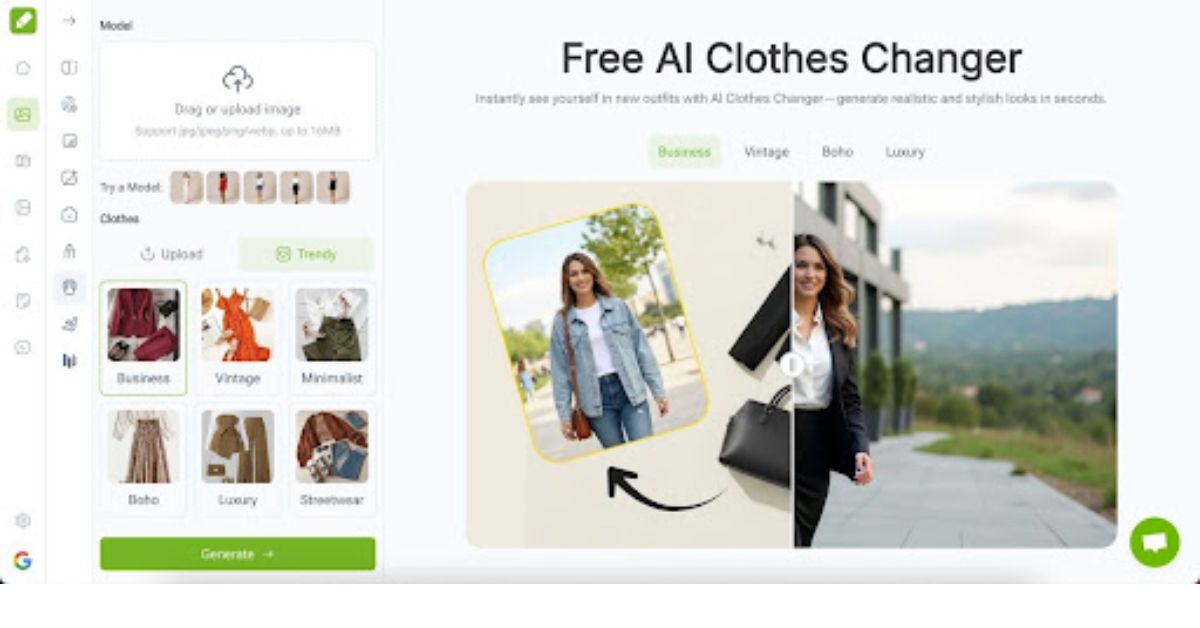
The Challenge Every Creator Faces In the fast-paced world of content creation, consistency and variety are everything. But for influencers, ...
Read moreHow to Download YouTube Playlist: Step-by-Step Guide

Downloading YouTube playlists can be incredibly convenient for people who want to enjoy videos or music offline without interruptions. Whether ...
Read moreFundamentals of Motor Circuit Protection: Key Concepts & Standards
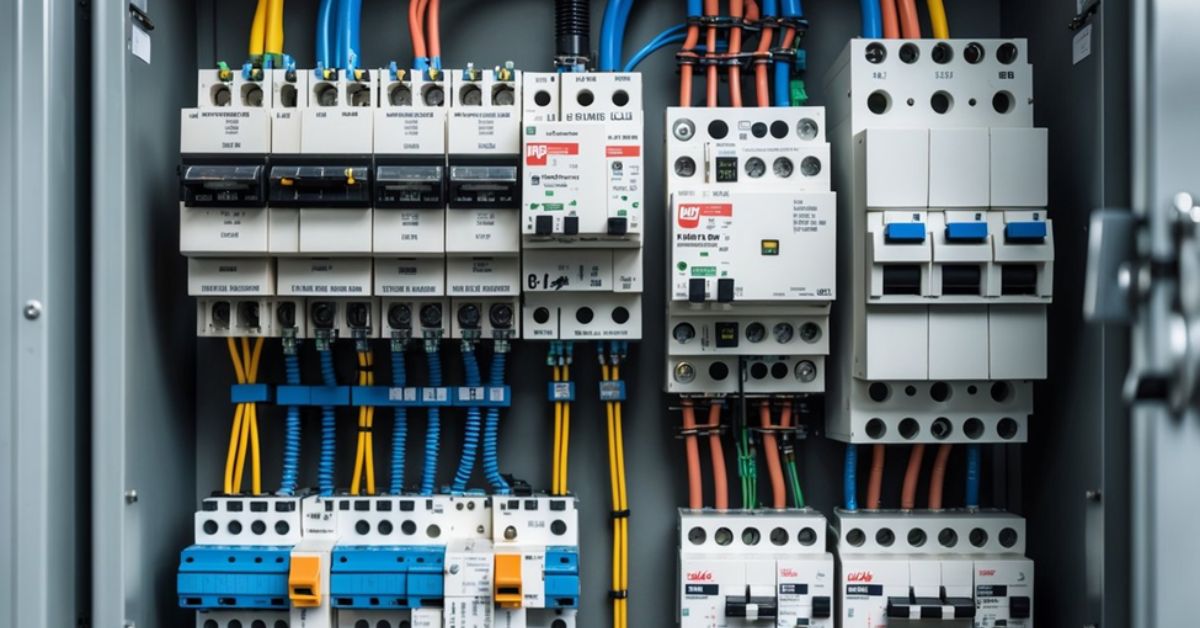
Motor circuit protection is essential for keeping electrical motors safe and working properly. It involves using devices that guard motors ...
Read moreWhy Charlotte WordPress Developers Are the Backbone of Local Businesses

Introduction Scroll through local listings in Charlotte and you’ll still find half-loading homepages, confusing navigation, and contact forms that may ...
Read moreThe Future of Software Development Lies in Human-Centric Design, Not Just AI

The conversation about innovation in technology is increasingly dominated by artificial intelligence. Every week brings a new announcement about AI-driven ...
Read moreHow Computer Vision Libraries Handle 3D Image Processing

Computer vision libraries have changed how we analyze digital images. They offer advanced tools for 3D image processing. These tools ...
Read more